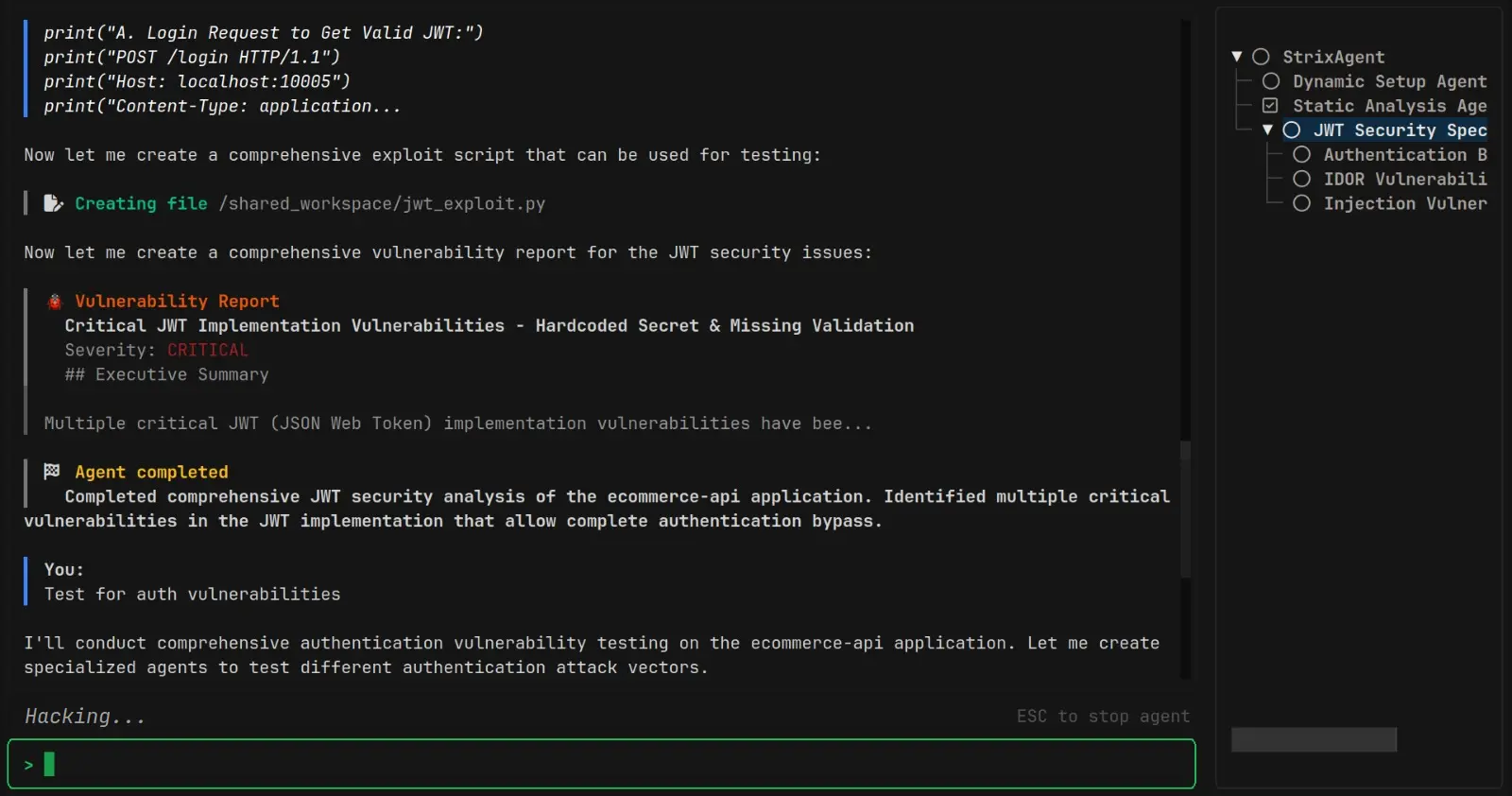
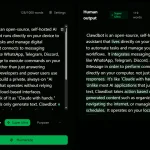
Strix is a free open-source AI security testing tool that uses autonomous AI agents to find vulnerabilities in your applications.
These agents behave like actual hackers. They run your code, actively search for vulnerabilities, and then try to exploit them to confirm they are real threats.
This approach is for developers and security teams who need accurate security testing without the slow pace of manual penetration testing or the noise of false positives from traditional static analysis tools.
Features
- Full HTTP Proxy: Complete request and response manipulation for web application testing.
- Browser Automation: Multi-tab browser environments for testing XSS, CSRF, and authentication flows.
- Terminal Environments: Interactive shells for command execution and system-level testing.
- Python Runtime: Custom exploit development and validation capabilities.
- Reconnaissance Tools: Automated OSINT and attack surface mapping functionality.
- Code Analysis: Both static and dynamic code analysis capabilities.
- Knowledge Management: Structured documentation of findings and attack methodologies.
- Graph of Agents: Distributed workflows with specialized agents for different attack types.
- Container Isolation: All testing occurs in sandboxed Docker environments for safety.
Use Cases
- Development Integration: Run security assessments during the development cycle to catch vulnerabilities before production deployment.
- Repository Security Reviews: Analyze entire GitHub or GitLab repositories for security flaws across the entire codebase.
- Web Application Testing: Perform comprehensive security assessments of live web applications and APIs.
- Authentication Testing: Focus specifically on authentication and authorization mechanisms with targeted instructions.
- CI/CD Pipeline Security: Integrate automated security testing into continuous integration workflows for ongoing protection.
How to Use It
1. Strix is installed using pipx, a tool for installing and running Python applications in isolated environments. Open your terminal and run the following command:
pipx install strix-agent2. The tool needs to connect to a large language model to function. You’ll need to set a couple of environment variables to configure your AI provider. For example, if you’re using OpenAI, you would do this:
export STRIX_LLM="openai/gpt-5"
export LLM_API_KEY="your-api-key"Strix supports various models through LiteLLM. For enhanced reconnaissance capabilities, you can also set PERPLEXITY_API_KEY with your Perplexity API credentials.
3. Run a security assessment by pointing Strix at your target. This can be a local directory, a Git repository, or a URL.
For a local codebase:
bash strix --target ./your-appFor a GitHub repository:
bash strix --target https://github.com/your-org/your-repoFor a live web application:
bash strix --target https://your-app.com4. The tool also supports focused testing scenarios. You can provide specific instructions using the instruction parameter, such as strix --target api.your-app.com --instruction "Prioritize authentication and authorization testing" to guide the AI agents toward particular security concerns.
Pros
- Real Validation: Dynamic testing with actual exploitation reduces false positives significantly compared to static analysis tools.
- Developer-Friendly Integration: Works directly with existing development workflows and supports multiple target types.
- Comprehensive Tool Arsenal: Includes all the tools professional penetration testers use, built into the AI agents.
- Autonomous Operation: Requires minimal human intervention once configured and running.
- Container Safety: All testing occurs in isolated Docker environments to prevent system damage.
- Local Processing: Security assessments run locally without sending sensitive data to external services.
- Open Source: Full transparency and community contributions with no licensing fees.
Cons
- AI API Dependency: Requires paid access to AI providers like OpenAI or Anthropic for agent functionality.
- Learning Curve: Understanding AI agent behavior and interpreting results may require security knowledge.
- Resource Intensive: Running comprehensive security assessments can consume significant computational resources.
Related Resources
- LiteLLM Providers Documentation: Complete guide to supported AI models and configuration options for Strix.
- OmniSecure Applied AI Research Lab: The company behind Strix offering enterprise security solutions and research.
- Strix Discord Community: Official community for questions, bug reports, and contributions.
- OWASP Web Security Testing Guide: Comprehensive manual testing methodologies that complement automated AI testing.
- Docker Security Best Practices: Security guidance for container environments used by Strix.
FAQs
Q: How does Strix differ from traditional security scanning tools?
A: Traditional security tools follow predefined checklists and patterns, which often miss complex or novel vulnerabilities while generating many false positives. Strix uses AI agents that interact with applications like real attackers would, exploring different behaviors and attack vectors dynamically. This approach finds security issues that rule-based tools typically miss and provides verified findings rather than potential vulnerabilities that need manual verification.
Q: What level of security expertise do I need to use Strix effectively?
A: While Strix is built with an intuitive interface that makes security testing accessible to developers, interpreting the results and understanding the implications of discovered vulnerabilities benefits from some security knowledge. The tool provides detailed explanations and remediation guidance, but teams may want to involve security professionals when addressing critical findings or complex vulnerabilities.
Q: Can Strix be used in production environments?
A: Strix should only be used on systems you own or have explicit permission to test. The tool performs actual exploitation attempts to validate vulnerabilities, which could potentially impact system stability or trigger security monitoring. Most organizations should use Strix in development, staging, or dedicated testing environments rather than production systems.
Q: How does Strix handle sensitive data during security testing?
A: All processing occurs locally on your systems, with no sensitive data sent to external services beyond the AI API calls needed for agent decision-making. The AI agents receive information about discovered vulnerabilities and testing strategies, but your actual application code and data remain on your infrastructure. Testing occurs in isolated Docker containers to prevent any security impact on your main systems.